Digital Asset Security: Why Investor Protection Matters

Gold and silver-backed digital assets command attention for investors searching for both stability and innovation. As digital currencies rapidly reshape financial expectations, managing their security has become a global priority. The reality is that protecting cryptocurrency investments requires far more than simple technological safeguards, especially given the evolving legal definitions and regulatory inconsistencies worldwide. This article will clarify common misconceptions, examine diverse security strategies, and help investors build confidence in their asset-backed tokens.
Table of Contents
- Defining Digital Asset Security And Misconceptions
- Types Of Asset-Backed Tokens And Security Needs
- How Custody, Audits, And Reserves Build Trust
- Key Investor Risks And Common Security Failures
- Best Practices For Protecting Your Investments
- Regulatory Compliance And Transparency Standards
Key Takeaways
| Point | Details |
|---|---|
| Understanding Digital Asset Security | Recognize that digital asset security involves a complex interplay of technological, legal, and financial factors beyond simple safeguards. |
| Nature of Asset-Backed Tokens | Different types of asset-backed tokens require tailored security strategies, focused on asset verification, liquidity management, and regulatory compliance. |
| Importance of Custody and Audits | Trust in digital assets is built through robust custody solutions, transparent reserve management, and regular independent audits. |
| Ongoing Regulatory Compliance | Investors must stay informed about evolving regulations and compliance standards to protect their interests in the digital asset ecosystem. |
Defining Digital Asset Security and Misconceptions
Understanding digital asset security requires navigating a complex landscape of technological innovation and regulatory uncertainty. Digital assets represent a revolutionary financial instrument that challenges traditional investment frameworks, creating unique security considerations for investors worldwide.
The emergence of decentralized digital assets (DDAs) has complicated traditional security definitions. Researchers exploring legal categorizations highlight critical challenges in classifying these assets as currencies, commodities, or securities. This ambiguity creates significant investor protection challenges:
- Lack of standardized regulatory frameworks
- Inconsistent international legal definitions
- Technological complexity obscuring true asset characteristics
- Variable risk profiles across different digital asset types
Security misconceptions often stem from oversimplifying digital asset characteristics. Unlike traditional financial instruments, digital assets require a multifaceted approach to protection that encompasses technological, legal, and financial dimensions. Evolving digital security landscapes demonstrate that protection strategies must continuously adapt to technological advances and regulatory shifts.
Investors must recognize that digital asset security extends far beyond simple technological safeguards. It involves understanding complex ecosystem risks, including:
- Blockchain infrastructure vulnerabilities
- Smart contract potential exploits
- Wallet and key management protocols
- Regulatory compliance challenges
The interconnected nature of digital assets means that security breaches can have cascading consequences across entire investment portfolios. Comprehensive protection requires a proactive, holistic approach that anticipates potential technological and regulatory risks.
Pro tip: Develop a dynamic security strategy that combines technological monitoring, legal awareness, and continuous education about emerging digital asset protection mechanisms.
Types of Asset-Backed Tokens and Security Needs
The digital asset landscape encompasses a diverse range of token types, each presenting unique security challenges and requirements. Digital asset classifications reveal complex security frameworks that demand specialized protection strategies.
Asset-backed tokens represent a sophisticated investment vehicle that bridges traditional financial instruments with blockchain technology. These digital assets derive their value from underlying physical or financial assets, creating a unique security ecosystem:
- Commodity-backed tokens (gold, silver, real estate)
- Stablecoins pegged to fiat currencies
- Fractional ownership tokens
- Investment fund representative tokens
Comprehensive digital asset research highlights critical security considerations for different token types. The protection requirements vary significantly based on the underlying asset and technological infrastructure, demanding a nuanced approach to risk management.
Investors must understand the specific security needs associated with different token categories:
Here is a quick reference overview of major types of asset-backed tokens and their distinguishing features:
| Token Type | Underlying Asset | Security Focus |
|---|---|---|
| Commodity-backed | Gold, Real estate, silver | Asset verification and authenticity |
| Stablecoin | Fiat currency, USD, Euro | Reserve transparency and liquidity |
| Fractional ownership | Physical assets, artworks | Ownership tracking and legal clarity |
| Investment fund tokens | Portfolio of assets | Regulatory compliance and auditing |
- Commodity-backed tokens require rigorous asset verification
- Stablecoins need robust liquidity and reserve management
- Fractional ownership tokens demand transparent ownership tracking
- Investment tokens require comprehensive regulatory compliance
Security in digital assets is not a one-size-fits-all solution but a dynamic, adaptive strategy tailored to specific token characteristics.
The interconnected nature of digital assets means that security vulnerabilities in one token type can potentially impact broader market stability. Comprehensive protection requires a holistic approach that combines technological safeguards, legal frameworks, and continuous monitoring.
Pro tip: Conduct thorough due diligence on the specific security mechanisms of each asset-backed token type before making investment decisions.
How Custody, Audits, and Reserves Build Trust
Digital asset custody represents the critical foundation of investor confidence in blockchain-based financial systems. Comprehensive digital asset custody strategies demonstrate the intricate relationship between technological infrastructure and investor trust.
Effective custody solutions encompass multiple layers of protection that go beyond simple asset storage:
- Secure cold storage mechanisms
- Multi-signature wallet protocols
- Regular third-party security audits
- Comprehensive asset tracking systems
- Transparent reserve management
Global regulatory frameworks highlight the critical importance of robust audit and reserve mechanisms in establishing investor confidence. Institutional-grade custody requires several key components that demonstrate financial integrity:
- Comprehensive asset verification processes
- Regular independent financial audits
- Transparent reserve documentation
- Real-time asset tracking capabilities
Trust in digital assets is not inherited but meticulously constructed through rigorous verification and continuous transparency.
The complexity of digital asset custody extends beyond technological solutions. Investors demand comprehensive proof of asset backing, which necessitates advanced verification mechanisms that combine technological sophistication with legal compliance.

Modern custody solutions must address multiple risk vectors simultaneously, creating a holistic protection environment that reassures investors about the safety and legitimacy of their digital holdings.
Pro tip: Always request and review detailed custody, audit, and reserve documentation before committing to any digital asset investment.
Key Investor Risks and Common Security Failures
Digital asset vulnerabilities represent a complex landscape of potential risks that demand sophisticated understanding and proactive management. Comprehensive investor risk assessments reveal multiple critical threat vectors that can compromise investment security.
The most prevalent security failures in digital asset ecosystems include:
- Inadequate custody controls
- Weak authentication mechanisms
- Software vulnerabilities
- Insufficient compliance practices
- Insufficient transaction monitoring systems
Digital asset system vulnerabilities demonstrate how seemingly minor security lapses can trigger catastrophic financial consequences. Cyber threats have evolved to target specific weaknesses in digital asset infrastructure:
- Social engineering attacks
- Wallet private key compromises
- Smart contract exploitation
- Insider manipulation risks
- Infrastructure penetration strategies
Investor protection requires constant vigilance and adaptive security strategies that anticipate emerging technological threats.
The interconnected nature of digital asset platforms means that a single vulnerability can potentially compromise entire investment ecosystems. Sophisticated attackers continuously develop advanced techniques to exploit technological and human-factor weaknesses in digital asset systems.

Investors must recognize that security is not a static condition but a dynamic process requiring continuous monitoring, updates, and proactive risk management approaches that adapt to emerging technological challenges.
The following table summarizes common investor security failures in digital asset ecosystems, their business impact, and recommended prevention strategies:
| Security Failure | Business Impact | Prevention Strategy |
|---|---|---|
| Weak authentication | Unauthorized asset access | Multi-factor authentication |
| Software vulnerabilities | Fund loss, reputation damage | Routine code audits and updates |
| Insufficient monitoring | Undetected fraud or theft | Real-time transaction monitoring |
| Compliance gaps | Regulatory penalties | Regular compliance reviews |
Pro tip: Implement multi-factor authentication and regularly update your security protocols to minimize potential digital asset vulnerabilities.
Best Practices for Protecting Your Investments
Digital asset protection requires a comprehensive, multi-layered strategy that goes beyond simple technological solutions. Security best practices for digital investments emphasize the importance of proactive and adaptive risk management techniques.
Critical security strategies for investors include:
- Implementing multi-factor authentication
- Utilizing diversified storage solutions
- Conducting regular independent audits
- Maintaining updated security protocols
- Continuously educating yourself about emerging threats
Comprehensive digital asset protection frameworks recommend a holistic approach to securing investments. Robust security measures should address multiple potential vulnerability points:
- Technical infrastructure protection
- Access control mechanisms
- Transaction monitoring systems
- Regulatory compliance tracking
- Incident response planning
Effective digital asset security is not about eliminating all risks, but about creating resilient systems that can adapt and respond to emerging threats.
Investors must recognize that security is an ongoing process requiring continuous attention and strategic adaptation. The digital asset landscape evolves rapidly, demanding a dynamic approach that anticipates and mitigates potential risks before they materialize.
Successful protection strategies integrate technological solutions with human expertise, creating a comprehensive defense mechanism that addresses both systematic vulnerabilities and potential human error.
Pro tip: Develop a comprehensive security checklist and review your investment protection strategy quarterly to stay ahead of emerging digital asset risks.
Regulatory Compliance and Transparency Standards
Digital asset regulations represent a critical framework for protecting investor interests in an increasingly complex financial landscape. Global regulatory trends demonstrate the complex challenges of establishing consistent international standards for digital asset governance.
Key compliance mechanisms include:
- Anti-Money Laundering (AML) protocols
- Know Your Customer (KYC) verification processes
- Transparent asset reporting requirements
- Cross-border transaction monitoring
- Regular independent audits
Digital asset privacy and regulatory frameworks highlight the delicate balance between investor protection and technological innovation. Regulatory standards must address multiple critical dimensions:
- Financial transparency
- Investor identity verification
- Transaction tracking mechanisms
- Data protection protocols
- Risk mitigation strategies
Effective regulation transforms digital assets from speculative instruments to legitimate, trustworthy financial tools.
The international regulatory landscape continues to evolve, with jurisdictions developing nuanced approaches that balance technological innovation with investor protection. Successful compliance frameworks require ongoing collaboration between technological experts, financial regulators, and legal professionals.
Investors must recognize that regulatory compliance is not a static condition but a dynamic process requiring continuous adaptation to emerging technological and legal challenges in the digital asset ecosystem.
Pro tip: Stay informed about regulatory changes by subscribing to official financial regulatory updates and participating in professional digital asset compliance forums.
Secure Your Future with Real Asset-Backed Digital Investments
Digital asset security is more than just a technical challenge It demands transparency trust and true backing by tangible resources to protect your investments against evolving risks Like the article explains investor protection requires rigorous custody audits and reserve validation to avoid pitfalls such as weak authentication or insufficient compliance At Maya Preferred we address these critical challenges head-on by offering blockchain tokens fully backed by physical gold and silver reserves supported by detailed proof documents and third-party audits
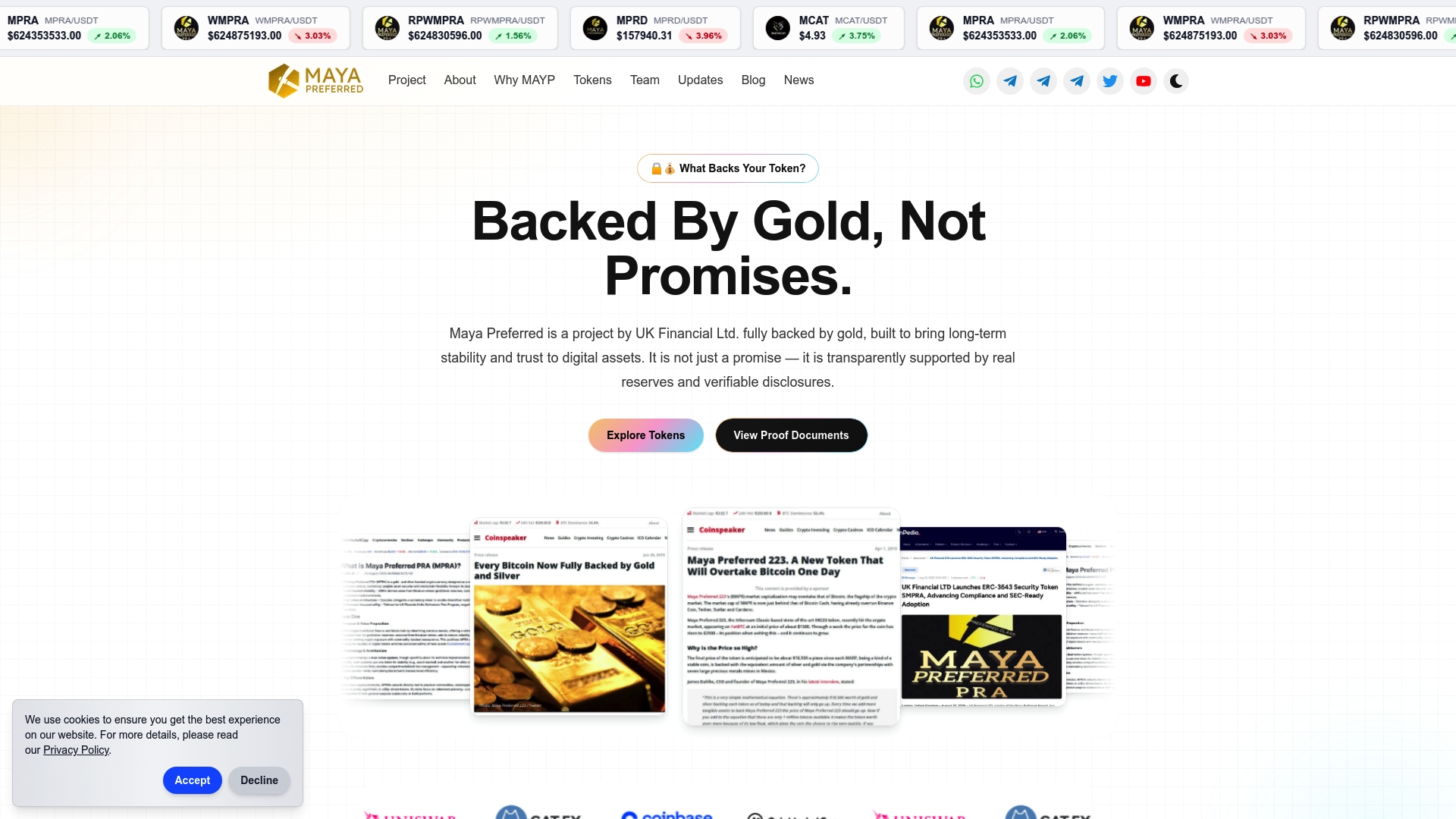
Don’t settle for digital assets with vague claims or hidden risks Discover how our MPRA MPRD and MCAT tokens bridge traditional precious metal investment with cutting-edge blockchain technology Visit Maya Preferred today to review our transparent reserve disclosures and regulatory compliance updates Gain confidence from our comprehensive security framework and take action now to secure a resilient and trustworthy digital asset portfolio
Frequently Asked Questions
What is digital asset security?
Digital asset security refers to the comprehensive measures and strategies implemented to protect digital assets—such as cryptocurrencies and tokenized assets—from theft, fraud, and technological vulnerabilities. It encompasses technological, legal, and financial dimensions for safeguarding investments.
Why do digital assets require a different security approach compared to traditional financial instruments?
Digital assets are inherently more complex due to their decentralized nature, varying risk profiles, and the involvement of blockchain technology. This complexity necessitates a multi-faceted strategy addressing unique technological, regulatory, and ecosystem risks.
What are the common vulnerabilities in digital asset ecosystems?
Common vulnerabilities include inadequate custody controls, weak authentication mechanisms, software vulnerabilities, insufficient compliance practices, and ineffective monitoring systems. Each of these can lead to significant financial losses and compromise investor security.
How can investors protect their digital assets effectively?
Investors can protect digital assets by implementing multi-factor authentication, utilizing diversified storage solutions, conducting regular independent audits, maintaining updated security protocols, and continuously educating themselves about emerging threats.
Recommended
- UK Financial Ltd Announces CoinMarketCap Supply Verification And Market Positioning Review For Regulated Security Tokens SMPRA And SMCAT | Maya Preferred
- UK Financial Ltd Executes Compliance Tasks Ahead Of First-Ever ERC-3643 Exchange-Traded Token, SMCAT & Sets Date For Online Investor Governance Vote | Maya Preferred
- Maya Preferred – Backed By Gold, Not Promises